T-Mobile subscriber narrowly escapes SIM swap fraud،
SIM swaps often require a shady representative to get involved in the crime
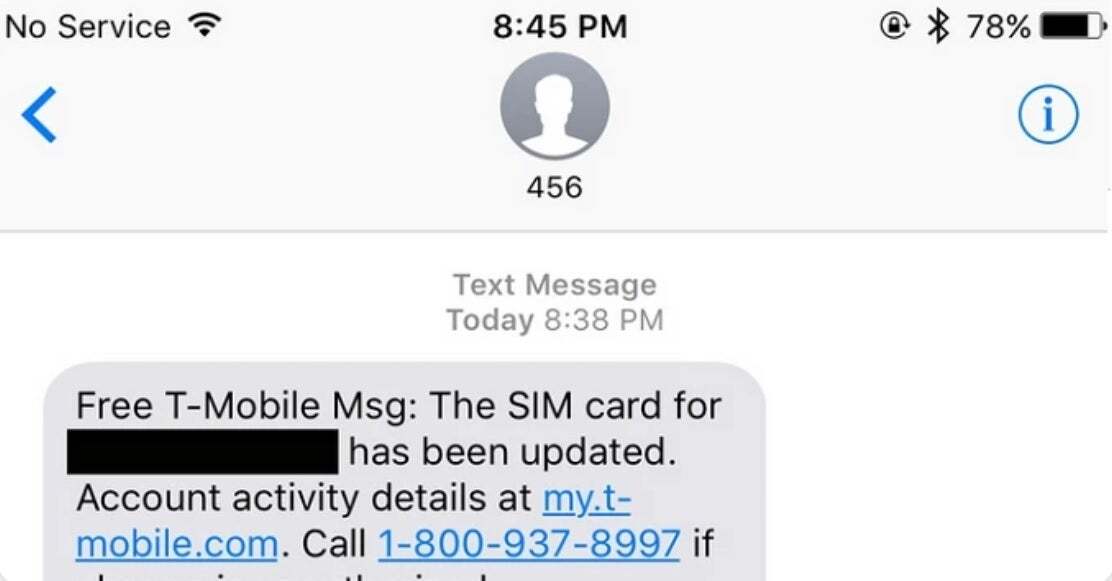
If you receive a text message like this but haven't requested a new SIM card, call your carrier immediately.
As time was running out, the man quickly called T Mobile even though it took an hour to explain to the rep what was going on. T Mobile was able to tell the concerned consumer exactly what had happened. Someone walked into a medical exam T Mobile store about 15 minutes from the victim's place of residence and pretending to be the victim, he asked for a new SIM card which was inserted into the thief's phone.
On the phone with T Mobile, the victim began receiving fraud alerts from their bank, which blocked expensive purchases of luxury items at department stores. The thief had changed the security settings of the T Mobile the customer's banking app and almost got away with it by making several purchases worth more than $10,000. When the T Mobile A customer tried to change the SIM card on his phone, the thief received a text message asking if he was trying to change his SIM card and he pressed “No”, which meant the bad guy continued to control the accounts of the victim.
This is what operators need to do to make SIM swaps more difficult for thieves.
You might ask why T Mobile failed to send the customer a text message asking them to verify the SIM swap when it initially occurred. This could have ended the whole scam in seconds. There are two answers. Firstly, if there is an intern working in the store, SIM swapping can be done without generating any text. And secondly, it is T MobileThe policy of not sending SMS if the SIM swap is carried out in one of its stores.
However, in-store SIM swaps must generate text BEFORE the change is made. In fact, any SIM card swap must generate text requiring an affirmative response from the device owner before any modification. This action needs to be taken by ALL carriers immediately, otherwise we are going to hear even more stories about their customers being scammed, having their bank accounts drained, and being responsible for expensive purchases they didn't make.
















