The Nothing CMF watch app was also discovered to have security flaws،
The Nothing Phone (1) and (2) have been praised in the past for having clean software – almost stock Android – with excellent home screen customization, and this has been the case since the first foray of the company in the smartphone OEM arena. However, as promising as that may be, the company hasn't had a good month when it comes to security.
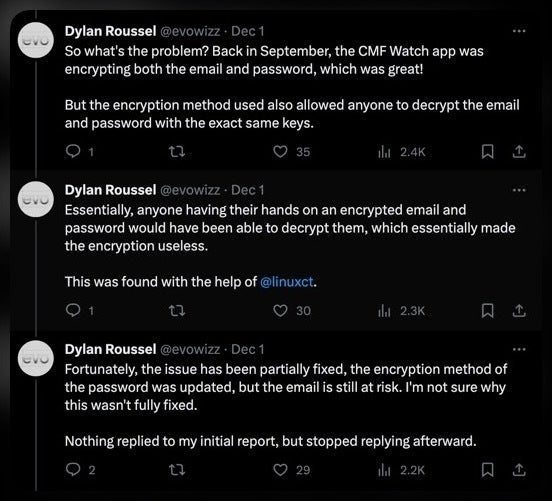
Source – Dylan Roussel | X
The CMF Watch app required users to create an account with an email address and password, and then the app encrypted that data. However, the app has also left the method of decrypting this data available within the app itself. This meant that a malicious actor could easily access this sensitive information.
CMF takes privacy issues very seriously and the team is investigating security issues regarding the Watch app. We resolved initial issues regarding credentials earlier in the year and are currently working to resolve the issues raised. As soon as this next patch is complete, we will roll out an OTA update to all CMF Watch Pro users. Security reports can now be submitted more easily via https://intl.cmf.tech/pages/vulnerability-report.
While it's great news that Nothing has recognized the problem and is taking the necessary steps to correct it, it's somewhat concerning that the company continues to find itself in this position. As a relatively new OEM, and especially one trying to get a new sub-brand off the ground, having vulnerabilities in your security is not a good idea. Hopefully, Carl Pei and his team have learned from this experience and do a better job of ensuring the security of their applications, especially when a third-party company is involved in the process.
Header image credit: https://intl.cmf.tech/
















